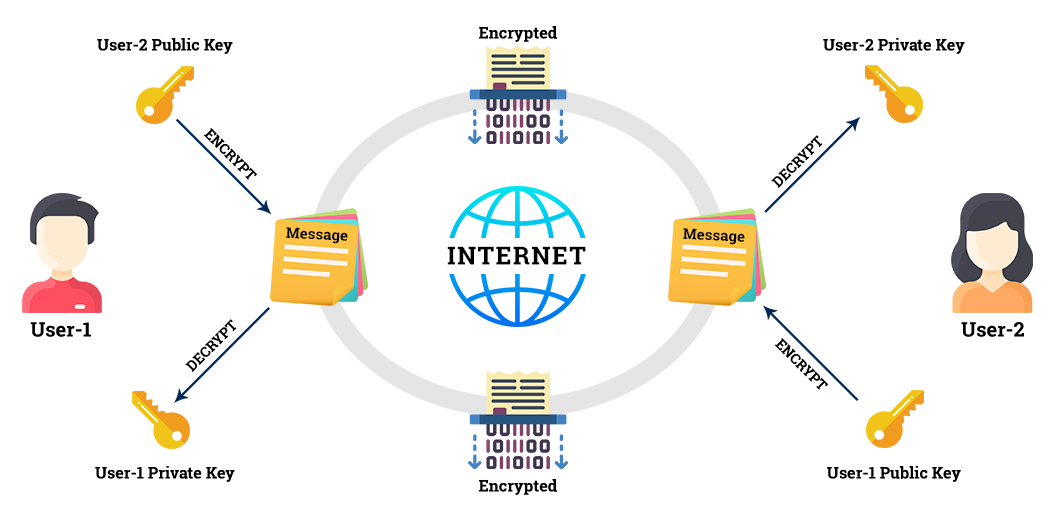
shopping online and recreational fields.
Understanding the Importance of AI in Personalization
AI plays a crucial part in advancing customization within context-aware recommendation systems. By processing extensive data, AI algorithms can uncover patterns and trends that influence user decisions.
AI significantly augments personalization in recommendation systems by scrutinizing data to discover user preferences.
Through this technology, we can provide tailored content, solutions, or products based on unique behavior, situational context, and historical interactions. Adaptive learning models regularly update based on updated data, boosting the relevance of advice over the course of time.
Moreover, AI facilitates real-time analysis, allowing for immediate modifications based on audience participation and outside influences. Through these capabilities, machine intelligence transforms ordinary products into customized interactions, ultimately driving user enjoyment and loyalty.
In conclusion, organizations leveraging AI for personalization can improve meet the diverse needs of their audience, developing deeper connections.
Analyzing User Preferences with Keytalk
Keytalk uses complex algorithms to analyze user activity patterns, providing understandings into individual preferences.
By grasping these models, the platform can adapt content delivery to elevate user engagement.
This specific customized strategy affirms that guidelines are suitable and timely, focusing on the personalized needs of every individual.
Analyzing User Behavior Patterns
When users use digital platforms, their interaction patterns reveal valuable insights into preferences and interests.
Keytalk applies advanced analytics to monitor user engagements, such as interactions, duration spent on particular content, and navigation routes. By analyzing these data indicators, Keytalk detects patterns and similarities among users, helping to build a robust profile of personal preferences.
This assessment not only points out popular features and content but also identifies hidden interests that might need acknowledgment. By noting changes in behavior over time, Keytalk can alter its tactics, ensuring that suggestions remain applicable and current.
Ultimately, understanding user behavior patterns facilitates Keytalk to enhance its approach, upgrading the overall user experience on digital platforms.
Personalized Content Delivery
Ensuring content connects with users, tailored content delivery depends greatly on the assessment of user preferences. Keytalk harnesses advanced algorithms to interpret user data, letting the platform modify content in real time. This strategy guarantees that users obtain applicable suggestions that reflect their unique preferences and actions.
Keytalk studies preferences through several methodologies, including:
- History of User Interactions: Tracking clicks and engagement metrics.
- Demographic Insights: Taking into account age, place of residence, and sex.
- Analysis of Content Consumption: Discovering frequently watched topics.
- Methods of Feedback: Employing user feedback through ratings and reviews.
- Social Media Engagement: Looking into shares and likes for more context.
Aspects Impacting Recommendations
Understanding the various elements affecting suggestions is important for increasing the efficacy of intelligent systems driven by AI. A range of factors adds to the quality of recommendations, including user behavior, preferences, and historical interactions.
Data about context, like the time of day, the location, and the device employed, greatly impacts tailored suggestions. Additionally, demographic information and societal impacts can further improve the recommendations presented to users.
Machine learning algorithms analyze these factors to identify patterns and predict user preferences, ensuring that the suggestions remain relevant and timely. The integration of diverse data sources ultimately enhances the comprehensive user interaction, making the recommendations more personalized and successful in fulfilling unique needs.
Boosting User Interaction with Customized Recommendations
Tailored suggestions can greatly enhance client participation by delivering bespoke content that resonates with individual preferences.
Through the use of contextual user insights, platforms can create enhanced relevant experiences that capture attention and promote interaction.
This process not only encourages a stronger link with users but also improves the likelihood of persistent engagement.
Tailored Content Distribution
As users move through the broad online landscape, personalized content delivery arises as a crucial tactic for boosting interaction. Through personalizing suggestions according to individual tastes and behaviors, platforms are able to boost user satisfaction and loyalty.
This strategy not only promotes more meaningful connections but also boosts conversion rates.
Important factors in personalized content delivery consist of:
- Analysis of User Behavior: Tracking interactions to understand preferences.
- Adaptive Suggestions: Offering suggestions in real-time according to latest trends.
- Segmentation: Sorting users according to interests for optimal content customization.
- Feedback Mechanisms: Fostering user responses to enhance recommendation accuracy.
- Advanced Learning Algorithms: Employing sophisticated analytics to forecast user demands.
These elements combine to form a more captivating and pertinent experience that connects with users.
Contextual User Insights
During the time that personal preferences influence content delivery, relevant user data further refine the method of personalization by considering the environment in which users connect with services.
Such insights encompass factors such as place, time period, kind of device, and even social settings, allowing for a deeper understanding of user patterns. By analyzing this content, AI systems can generate specific suggestions that resonate with users in instantaneously, thereby enhancing engagement.
By way of example, a user browsing a travel site during their lunch break might receive travel recommendations that align with their short-term travel goals.
As a result, situational user insights bridge the gap between unchanging preferences and adaptive user experiences, fostering intimate connections and increasing the likelihood of response to advised content.
Applications of Keytalk's Solutions
The advancements from Keytalk has found multiple applications across many industries, overhauling how businesses engage with their users. By leveraging situational recommendations, companies can enhance customer experiences and drive profits.
Several significant applications consist of:
- Digital Commerce: Tailored shopping journeys based on user behavior and preferences.
- Tourism and Accommodations: Personalized travel advice and itinerary planning for individual travelers.
- Healthcare Sector: Tailored health solutions and treatment plans based on patient data.
- Media and Entertainment: Tailored viewing suggestions for streaming services, improving viewer satisfaction.
- Shopping Industry: Enhanced in-store experiences through location-based promotions and offers.
These examples highlight Keytalk's skill to transform customer interactions, making them more meaningful and effective across diverse sectors.
Keytalk's advancements enhance customer interaction, guaranteeing that interactions are increasingly significant and productive across a range of fields.
Utilizing this technology indicates a transition towards a more individualized business framework.
The Benefits of Context-Aware Recommendations
Context-specific recommendations deliver important advantages by refining user satisfaction through personalized advice.
They make large-scale personalization possible, letting businesses effectively address unique preferences.
Consequently, this technique results in boosted interaction metrics as users find more relevant content and products.
Elevated User Experience
While users journey through digital platforms, the opportunity to receive bespoke recommendations according to their unique circumstances profoundly elevates their overall experience.
Tailored suggestions foster a flawless interaction, ensuring that users access relevant content simply. This yields a highly engaging and pleasurable user journey.
Key advantages include:
- Boosted Relevance: Suggestions align closely with current needs and interests.
- Time Optimization: Users cut down the time required to discover relevant content.
- Boosted Engagement: Customized recommendations promote richer interactions.
- Improved Satisfaction: Individuals sense acknowledgment and appreciation from the service.
- Increased Retention: Favorable experiences inspire frequent user returns.
Personalization at Scale
Even though several digital platforms focus on offering individualized interactions, attaining widespread personalization remains a substantial obstacle.
Recommendations that are context-aware utilize artificial intelligence to analyze customer behavior, preferences, and situational factors, enabling a bespoke solution that adapts to unique preferences. This technology promotes the delivery of contextually appropriate content and resources, enhancing customer satisfaction and allegiance.
By harnessing vast amounts of data, organizations can discover insights that inform intelligent recommendations and recommendations. Consequently, businesses can reach a variety of customer segments more successfully, leading to higher conversion rates plus customer retention.
At last, the application of adaptive suggestions facilitates a more engaging user experience, connecting unique preferences and mass application, thereby transforming how marketers reach their target audiences.
Boosted Engagement Rates
How might enterprises effectively boost user engagement in an increasingly competitive digital landscape?
AI-powered suggestions powered by AI serve as a key resource to enhance user engagement. By providing tailored suggestions based on users' actions and likes, businesses can enhance their engagement.
The gains from these recommendations consist of:
- Improved customer satisfaction by providing tailored content.
- Improved purchase rates because users discover offerings that meet their requirements.
- Increased retention rates due to tailored experiences fostering return visits.
- Enhanced brand loyalty resulting from fulfilling user interactions.
- Deeper knowledge of customer behavior, facilitating more successful marketing approaches.
Utilizing context-aware recommendations has the potential to revolutionize client interaction and boost business outcomes.
Exploring Keytalk's Algorithm
The algorithm by Keytalk is prominent in the field of context-sensitive suggestions thanks to its novel strategy for merging behavioral data and external variables.
Through the use of data-driven learning strategies, the algorithm processes current data, including placement, timestamp, and user behavior, to produce tailored recommendations. This adaptable adaptability allows Keytalk to enhance its projections constantly, boosting user experience.
In addition, the algorithm makes use of collaborative filtering and content-based methods, ensuring a thorough understanding of user preferences. The result is a sophisticated system capable of delivering personalized recommendations that resonate with users on different facets.
This algorithm merges collaborative filtering with content-based approaches to deeply understand user preferences for individualized recommendations.
The focus on context by Keytalk enhances not just accuracy but also creates stronger engagement, making it a pivotal tool in the landscape of AI-driven recommendation systems.
Futuristic Trends in AI-Driven Personalization
The development of algorithms that are aware of context, such as those employed by Keytalk, sets the stage for future trends in AI-enabled personalization.
With the development of technology, a number of key trends are poised to arise:
- Refined User Profiling: Utilizing deeper insights into user behavior and preferences.
- Instant Adaptation: Algorithms that adjust recommendations instantly based on live data.
- Multimodal Interaction: Incorporating sound, text, and imagery for a fluid interaction.
- Data Privacy Centered Approaches: Aligning personalized solutions with user privacy assurance and data protection.
- Inter-Device Synchronization: Offering standardized recommendations over a range of devices and interfaces.
These developments suggest a transition to more user-friendly and personalized approaches, significantly improving the overall experience for users.
Beginning Your Journey With Keytalk's Suggestions
Exploring the effectiveness of Keytalk's suggestions begins with understanding its sophisticated algorithm engineered to interpret user context thoroughly. This algorithm utilizes diverse data points, including user actions, desires, and up-to-date situations, to deliver specific insights.
To get started, users should integrate Keytalk's API into their applications, enabling effortless data sharing. Post-installation, it's important to establish user profiles and adjust settings for better recommendations. Regularly updating these profiles enhances the algorithm's accuracy over time.
Furthermore, utilizing analytics tools provided by Keytalk allows track engagement and refine recommendations further. By following these steps, businesses may exploit the power of adaptive recommendations, ultimately improving customer experience and driving engagement.
Keytalk's innovative approach sets a new standard in customized communications.
Frequently Inquired Questions
How Does Keytalk Ensure User Data Privacy and Security?
The question of how a company guarantees user data privacy and protection is vital in today's digital age.
Keytalk applies advanced encryption methods for the protection of sensitive information and abides by strict data protection regulations.
Also, they perform periodic security audits and adopt anonymization techniques to defend user identities.
Can I Customize My Recommendation Settings in Keytalk?
Are users able to personalize their experiences to match their tastes? In the domain of customization tools, personalization is frequently a critical aspect.
Users can indeed adjust their recommendation settings, allowing for a more tailored engagement. This flexibility enables people to refine the types of suggestions they receive, ensuring that the content aligns with their interests and needs.
Ultimately, this level of customization enhances customer happiness and engagement within the platform.
Is Keytalk Compatible With All Devices and Platforms?
One compatibility of Keytalk with multiple hardware and systems constitutes an crucial factor to prospective users.
Typically, it is built to function effortlessly across various software environments and devices, including handheld devices, tablets, and laptops.
Nonetheless, particular compatibility may rely on the device's specifications and the software version.
Users are prompted to check the official documentation for detailed information regarding supported platforms to guarantee peak functionality.
Frequency of Updates for Recommendations by Keytalk
The level of updates for proposals changes depending on the exact approaches and material used.
Typically, systems like Keytalk aim to revise their recommendations in real-time or at regular intervals to guarantee pertinence. This may involve frequent learning from user behavior and likes.
How Can Various Industries Take Advantage of Keytalk's Context-Aware Recommendations?
Several fields can greatly improve through context-sensitive recommendations, for example, retail, where tailored shopping experiences enhance customer satisfaction.
The health industry can use personalized advice to support patient care and treatment solutions.
Furthermore, the hospitality industry can improve guest experiences through bespoke service advice.
In addition, education can harness these insights to provide personalized learning pathways for students, making the advice applicable across multiple fields that emphasize user engagement and satisfaction.
Summary
Within the dynamic world of digital engagement, Keytalk emerges as a lighthouse, guiding users through the fog of information with personalized insights. By harnessing the power of smart algorithms, it tailors suggestions that resonate deeply with specific needs, much like a skilled artist who paints a unique portrait for each admirer. As the tides of bespoke services continue to rise, Keytalk stands poised to illuminate pathways, enhancing Come 2025, Keytalk will overhaul the authentication of devices through the use of state-of-the-art cryptographic approaches and a framework of zero trust. Their approach concentrates on multi-step authentication and perpetual verification, advancing security across various sectors, including the finance and healthcare sectors. By leveraging decentralized management of identities, Keytalk lessens threats linked with breaches that are centralized. This cutting-edge approach not only safeguards sensitive information but also improves user interactions. Such advancements open up opportunities for a safer digital environment in the future. Why is upgraded device authentication becoming essential in today's online ecosystem? As more devices become interconnected, so does the risk of illicit access and security breaches. Cybercriminals continuously exploit vulnerabilities, making secure authentication practices essential for organizations and individuals alike. Enhanced device authentication provides a layered security, incorporating advanced technologies such as biometric identification, device tokens, and automated learning algorithms to verify user identities and the security of devices. This proactive approach helps mitigate risks associated with stolen credentials and insecure devices. In an era where remote work and digital transactions are commonplace, ensuring that only authorized devices gain access to critical details is crucial. Boosting access controls fosters trust and security in an interconnected world, safeguarding key data against evolving threats. Zero Trust has emerged as a critical component in modern security frameworks, emphasizing the principle of "Trust No One". This method requires constant assessment of every individual and device wanting to gain access to resources, regardless of their location within or outside the network. As institutions deal with rising security challenges, grasping the importance of Zero Trust is vital for strong device authentication strategies. As entities encounter more advanced cyber threats adopting a Zero Trust model has become imperative to modern security frameworks. This method stresses the principle of "Trust No One," requiring thorough scrutiny for every user and device, regardless of their location. Understanding that threats could be present both internally and externally, Zero Trust cultivates a heightened security posture. Organizations implement precise micro-segmentation to limit access to sensitive data, ensuring that users only have the permissions necessary for their roles. Moreover, uninterrupted monitoring and analysis of user behavior become critical components, enabling swift identification of potential breaches. This paradigm shift not only fortifies defenses but also fosters a culture of security preparedness, which is essential for navigating the complexities of today's digital landscape. The implementation of a Ongoing Verification Process represents a natural evolution of the Zero Trust architecture, reinforcing the principle of regular scrutiny within security measures. This approach guarantees that every user and device is continuously evaluated, rather than relying on a one-time verification at the point of entry. As organizations face growing dangers, the Continuous Verification Process becomes essential in maintaining solid safety. Decentralized identity management represents a transformative shift in how private data is handled. By distributing control over identity information, this approach improves privacy and allows individuals to oversee their personal data. While organizations strive to improve security strategies, the role of decentralization becomes ever more vital in terms of device authentication. Typical identity management systems tend to focus power in a sole entity, decentralized identity solutions presents an innovative strategy to boost security and user empowerment. This shift enables individuals by granting them the power to manage their identity autonomously, reducing the risks associated with centralized information breaches. This method reshapes the concept of trust in digital interactions, fostering a better safeguarded online environment. As more individuals look to regulate Learn More their private information, enhanced privacy becomes a fundamental aspect of identity management without centralization. This innovative approach enables users to verify their identity without depending on centralized bodies, markedly reducing the risk of security infringements and identity theft. By utilizing distributed ledger systems, individuals can manage their identities through secure, cryptographic methods that guarantee only necessary information is shared with third parties. This adjustment allows users to choose which information is shared and with whom, fostering assurance and visibility. In addition, decentralized identity administration decreases the retention of sensitive data on centralized systems, thereby enhancing overall protection. As the demand for privacy intensifies, this innovative approach offers a promising solution for secure and user-centric identity management. Keytalk is known for its innovative approach to ensuring device safety leverages sophisticated encryption methods to enhance identification processes. By integrating robust security measures, the company aims to provide a stronghold for interactions for device connectivity. This system not only defends against unauthorized access but also secures the authenticity of data along with confidentiality throughout device communication. With these tactics, Keytalk notably enhances the security landscape, situating itself as a leader in device authentication solutions for the future. To improve the experience for users while preserving protection, institutions must utilize user-friendly authentication processes that emphasize convenience and efficiency. This method involves implementing multi-factor authentication that is simultaneously simple and effective, allowing users to access devices seamlessly while upholding strict security protocols. Through the integration of biometric solutions, for example fingerprint and facial scans, organizations can lessen friction during the sign-in process, making it more accessible. Additionally, using single sign-on approaches can lessen the number of credentials users need to retain, further improving accessibility. It is vital for organizations to pay attention to clear communication and support, enabling users to navigate security protocols easily. Balancing convenience and security ultimately leads to increased user happiness and greater alignment with security regulations. While many organizations seek innovative solutions for secure authentication, technology from Keytalk excels with its effective uses in various sectors. Its functionality strengthens security while facilitating user experiences, making it an ideal choice for businesses aiming to protect sensitive data. Keytalk's robust features enable organizations to integrate secure authentication effortlessly. These examples highlight Keytalk's ability to adjust and deliver secure security measures across diverse sectors. As fields increasingly integrate advanced authentication technologies for example Keytalk, the area of device authentication is primed for notable advancements. Anticipated changes are expected to focus on enhancing security protocols through the integration of automated intelligence and data-driven learning, enabling real-time threat detection and response. In addition, the growth of the Internet of Things (IoT) will require scalable solutions designed to manage a high number of devices efficiently while sustaining effective security safeguards. Blockchain tech is likely to be essential in building autonomous authentication networks, diminishing reliance on main authorities. In addition, user-centric approaches will likely gain traction, prioritizing seamless user experiences without compromising security. This information implies a future where device identification becomes ever more adaptive, insightful, and resilient against rising cyber threats. The inquiry centers on how a particular solution guarantees compatibility with existing authentication systems. Usually, such methods involve using uniform protocols and APIs that facilitate transparent integration. By adhering to market standards, the solution can work alongside various authentication mechanisms without requiring extensive modifications. Also, thorough testing and feedback mechanisms with end-users help uncover potential conflicts, guaranteeing that the compatibility remains dependable and functional across different platforms and technologies. A range of industries stand to gain considerably from advanced device authentication solutions. Surprisingly, healthcare organizations benefit by securing confidential patient information, while financial institutions enhance security measures to protect against fraud. Furthermore, the manufacturing sector can safeguard patented information and proprietary information. Businesses in retail also appreciate the significance of securing customer transactions and personal data. One may believe that old technology are ultimately fated to become obsolete, yet Keytalk's technology offers a surprising lifeline. This solution effectively accommodates older systems, merging advanced authentication methods while maintaining compatibility. This situation underlines an essential advantage: organizations can boost security without losing their current setup. Cost factors involved in utilizing cutting-edge authentication techniques may fluctuate significantly depending on various elements. These include the deployment scale, the complexity of existing systems, and specific organizational needs. Often, organizations are required to think about initial setup costs, regular maintenance fees, and possible training costs for employees. Additionally, the integration of such solutions with legacy systems may incur further costs, highlighting the importance of a comprehensive budget evaluation prior to implementation. User information protection through login procedures is crucial to copyright privacy and security. Advanced cryptographic techniques are employed to secure confidential information, ensuring it remains inaccessible to unauthorized users. Additionally, two-factor authentication fortifies security by requiring multiple verification steps. Frequent security audits together with updates help spot vulnerabilities, while awareness training for users further minimizes risks. In the changing digital world, the outlook for device verification is akin to a stronghold, where Keytalk Systems being its attentive protector. Adopting a blend of fresh security solutions, the approach brings together fluid user experiences alongside powerful safeguards. With each passing year, the horizon brightens with the promise of autonomous identities and Zero Trust security models, depicting a scene of a universe where devices connect effortlessly, defended from unseen perils, and empowering users with confidence and peace of mind.Supercharge Device Authentication in 2025 – Secured by Keytalk
Key Takeaways
Acknowledging the Significance of Enhanced Device Authentication
Adopting Zero Trust in Modern Security Systems
Believe No One
Endless Validation System
A Fresh Perspective on Identity Management
Value of Decentralization
The benefits of decentralization consist of
Superior Privacy Control
Keytalk's Cutting-Edge Method for Securing Devices
Improving User Experience With Robust Security
Utilizing Keytalk Technology in the Real World
Keytalk technology is renowned for providing robust secure authentication solutions across various sectors.
Looking Forward: Device Authentication Insights
Frequently Inquired Questions
How Keytalk Confirms Interoperability With Existing Authentication Solutions?
Which Industries Find Keytalk's Device Authentication Solutions Most Beneficial?
Can Keytalk Help Legacy Devices?
What Are the Financial Implications of Using Keytalk's Solutions?
How Are User Details Guarded Throughout Authentication?
Final Thoughts